- Case StudyHelp.com
- Sample Questions
Chapter 1
Introduction
- Overview
Several studies have revealed that many organizations start considering cloud computing as a best choice to handle their huge amount of data. Cloud is an environment of the hardware and software resources in the data centers that provide diverse services over the network or the Internet to satisfy user’s requirements [1].
Over the last few years, data has become one of the most important assets for companies in almost every field. Not only are they important for companies related to the computer science industry, but also for organizations, such as countries’ governments, healthcare, education, or the engineering sector.
In 2003, five Exabyte’s of data were created by humans, and this amount of information is, at present, created within two days [2]. The rate at which new data are being generated is staggering [3]. This increment in the data volume which captured from lot of sources like Social media, Internet of things (IOT), Sensors and other data sources which produce Structured, semi-Structured or unstructured data are called Big Data.
Furthermore, this data is mostly unstructured, signifying that traditional systems are not capable of analyzing it. Organizations are willing to extract more beneficial information from this high volume and variety of data [4]. As new technology there are many issues related to Big Data, these issues are related not only to the volume or the variety of data, but also to data quality, data privacy, and data security. This effect brings a question of security and privacy that every organization should put into consideration. The key challenges in cloud computing include the loss of trust, control and multitenancy. And this is poses a very huge challenges in big data for every organization. This research will this addressing the current technologies and other advancement that have been put in place so as to enhance big data privacy and security in cloud computing.
This thesis discusses the security and privacy challenges of big data challenges faced by such organizations with identifies some of the known solutions to describes how cloud computing can be used to provide innovative solutions that ensure the safety of Big Data
2 Problem Background (200 Word)
هنا هنذكر طبيعة Big Data وازاى بتسبب مشكله
While the internet grew rapidly and Cloud Computing is expanding as a service used by a great number of many individuals and organizations internationally, Security issues related to Big Data in Cloud Computing are not being widely discussed or considered.
Many organizations that handle sensitive information are considering using cloud computing as it provides resources that can be scaled easily, along with significant economic benefits like The usability, accessibility, low cost and the high volume of available information related to the Cloud Computing raise a range of important policy issues, which include issues of privacy, security, anonymity, telecommunications capacity, government surveillance, reliability, and liability, among others.
This thesis discusses the Big Data Security challenges faced by such organizations and describes how Big Data can be more Secure with providing a model to cloud computing can be used to provide innovative solutions that ensure the safety of sensitive information.
The main focus of this thesis is on Big Data Security Challenges
Cloud architecture is fundamentally different from other systems, the Cloud environment is by nature multitenant with shared resources, and the location of the data and the local privacy requirements will not be controlled by the user. It is important to have in our mind that Cloud is enabled by virtualization technologies.
The Problem of Cloud Computing security is very important and can prevent the rapid growth. But what is the problem exactly? And why do we need a Security Policy for the Cloud Computing? We analyze the problem of security in Cloud and its strategy in accordance with the concepts and characteristics of Cloud Computing.
Many of the security issues that need to address the Cloud Computing are already known in other systems. But the Cloud Computing system has certain characteristics and attributes that create new security concerns.
Firstly, the Cloud environment has a much more complex architecture compared to other systems.
3. Problem Statement (150 Word)
Do we have appropriate model to improve Big Data Security which stored in cloud computing? This study aims to investigate of the main challenges and problems that can be found with respect to the topic of Big Data security
if the stakeholders of Big Data which stored in cloud computing data are aware of the security challenges related to store data in cloud. Users may be unaware of such risks or may simply be unconcerned, along with another question whose objective is to discover the main security …….. Finally, we wished to discover …….
4 Research Questions
The objective of this research is to examine levels of awareness of Big Data security challenges by answering the main question “How Big Data Security in Cloud Computing affect the end-user trust and engagement”.
- RQ1 What are the main challenges and problems with respect to Big Data security?
- RQ2 What kinds of research have been proposed with respect to Big Data security?
- RQ3 What models can be used to increase Big Data Security in Cloud Computing?
- RQ4 what are the major Big Data security challenges we might face in future?
- RQ5 How can we handle Big Data security challenges that are expected in future?
5 Research Objectives
The main objective of this research is to proposed a model to Enhance Big Data security which stored in Cloud Computing for Public sectors, in order to achieve this, we will investigate the security challenges in the context of Big Data by performing cross-cultural study.
The main objectives of this research are:
- Identify the most important Security challenges for Big Data in cloud computing
- Addressing relationship of Big Data Security concerns and trust & engagement
- Propose and validate a model to increase Big Data Security in cloud computing
6 Research Scope (150 Word)
Throughout This study the author is going to use quantitative methodology to focus on Security concerns generate by Big Data in Cloud Computing. This research aims to investigate the consumer perspective from 360-degree point of view which include (End User, Technical, Government and Service Provider)
7 Research Significant and Motivations (150 Word)
Because this research is investigating the potential security challenges that are associated with Storing Big Data in Cloud Computing, it is hoped that it will be beneficial for the academic researcher, universities, End-users and Governments. These users could use the research to gain a deeper understanding of the underlying issues relating to Big Data Security in cloud computing in order to help mitigate these challenges.
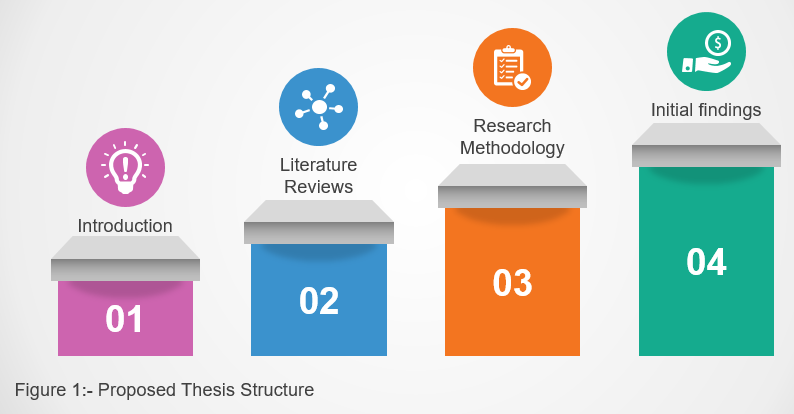
8 Proposed Thesis Roadmap
The Structure of the Proposed thesis is organized as follows:
- Chapter 1- Introduction. discusses a brief introduction of the proposed study, the context of the study, research problem and overview of the research questions as well.
- Chapter 2 – Literature Reviews. discusses Big Data and Cloud Computing background and Information System Theories.
- Chapter 3 – Research Methodology. discusses the methodology used for this research
- Chapter 4 – Initial findings. will present the initial findings of the research and analysis of these findings.
9 Chapter Summery
This chapter provides an overview of the proposed thesis, introducing problem background, research problems which lead to the research questions and research objectives formulation. The scope and significance of the study that will be discussed. Finally, the organization of the proposed thesis that will be provided.
Chapter 2
Literature Review- Big Data Security Challenges in Cloud Computing
- Overview (200 Word)
- Big data Overview
- Big Data Definition (200 Word)
- Big Data Characteristics (250 Word)
- Big Data Life Cycle (150 Word)
- Big Data Classifications (150 Word)
- Benefits of Big Data for Public & private Sectors (300 Word)
- Cloud Computing Overview (200 Word)
- Essential characteristics of cloud computing (350 Word)
- Cloud Computing Service Delivery Models
- IaaS
- PaaS
- SaaS
- Cloud Computing Deployment Models
- Public
- Private
- Community
- Hybrid
- Virtual Private
- Benefits of Cloud Computing (300 Word)
- Importance of Big Data Security in Cloud Computing (500 Word)
- Big Data Security Challenges and issues in Cloud Computing (4900 Word)
- Relevant Theories Overview (150 Word)
- Diffusion of innovation Theory
- Stockholder Theory
- Deleon & Maclean Success Theory
- Technology Acceptance Model
- Conclusion (100 Word)
Chapter 3
Research Methodology
- Overview (150 Word)
- Research Paradigm
- Research Approach
- Research Design
- Research Phases
- Phase 1: Problem identification
- Phase 2: Research Model Development
- Phase 3: Data Collection and Sampling Strategy
- Phase 4: The Survey
- Phase 5: Thesis Writing
- Research Ethics
- Chapter Summery
- Lesson Learned
Big data security: issues, challenges, Solution & concerns – Get Professional assignment help with US
We help with Phd Proposal on Big Data security issues in Cloud Computing
Security Issues in Big Data Research Papers
Big Data Privacy and Security Challenges
Big Data Security and Privacy Issues and Solutions